
There are several things that need to be bolded for every py programmer to be used or to have information on how and why is used.
Type hints
Python 3.5 brings type hints for clear function/interface usage. Idea is to set proper input instead of sending different type variables. Example of bad code:
def greeting(name):
return 'Hello ' + name
Here we can pass numbers, boolean, or another complex object (class, function) and produce issue.
The clean version goes:
def greeting(name: str) -> str:
return 'Hello ' + name
If you have 1000 lines inside of your codebase, for sure you don't understand this approach. But if your code goes up to 10 million lines of code - this seems really good practice.
Assignment expressions
In version Python 3.8 you have assignment expressions where is possible to use ":=" as part of a larger expression.
if (n := len(a)) > 10:
print(f"List is too long ({n} elements, expected <= 10)")
This is good and not good. Let me explain why. A a person who lives in Py world, this lead me to think what would do programmer that don't take time to make clean code. Example of growing expression:
if (n := len(c := (d := a.replace("a","g"))[:len(a)])) > 10:
print(f"List is too long ({n} elements, expected <= 10)")
Clean code could be:
a = "asdasdasdasdasdasd"
d = a.replace("a","g")
c = d[:len(d)]
if (n := len(c)) > 10:
print(f"List is too long ({n} elements, expected <= 10)")
This is why a new approach could lead to messy code.
range() and xrange() in Py2.x
People still using Python 2.x. Some of the usages are in web services. Sometimes they need to produce a bunch of IDs from 1 to 100 million. One approach is to use range() which return list. xrange() return generator object. What is the difference between them? In the first case, range, it uses large amounts of memory to set all numbers (integer, 4 bytes) into memory. So 100 000 000 x 4 is a lot of memory. Generator object objects that produce next() value and using just one size of integer for memory. This is used for example subnet generator, and picking up the second IP from the list. So imagine if you have 1000 subnets to generate each time with range() and xrange(). This happened before and I saw the issue. Change from range() to xrange() brings better work with memory and stopped to crashing web services.
New Dictionary algorithm
In Python 3.6 is introduced a new algorithm for dict objects. Proposed by Raymond Hettinger on Py Dev list New Dict proposal it brings between 20% and 25% smaller compared to Python 3.5. Good video on this topic is Raymond Hettinger Modern Python Dictionaries
asyncio — Asynchronous I/O, event loop, coroutines and tasks
It was introduced in Python 3.4. From the official documentation: "This module provides the infrastructure for writing single-threaded concurrent code using coroutines, multiplexing I/O access over sockets and other resources, running network clients and servers, and other related primitives" Asyncio usage
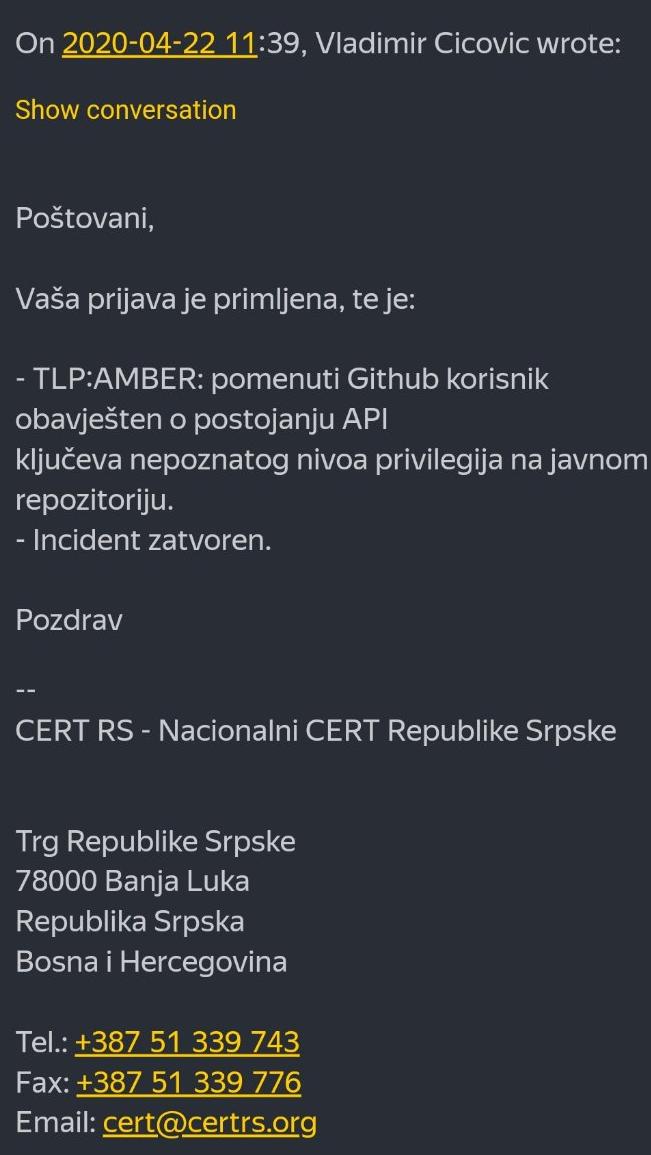
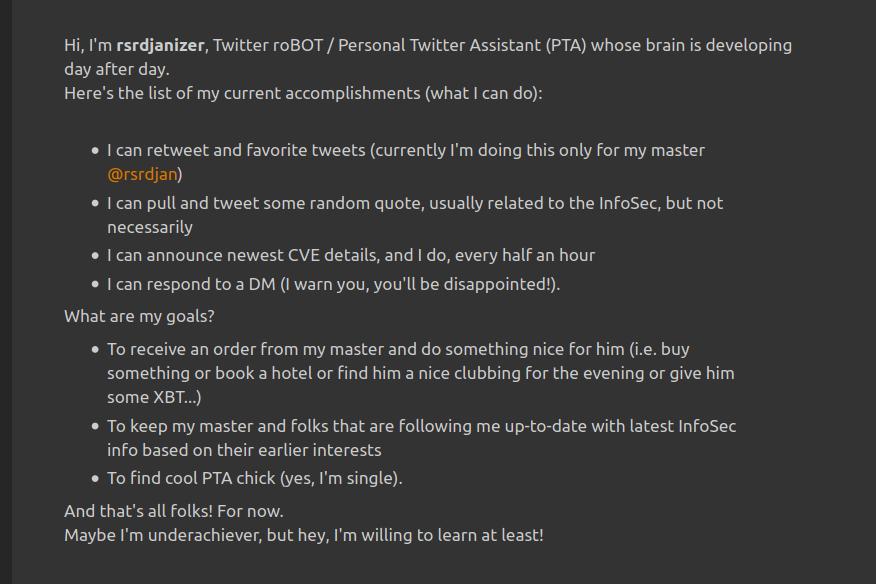
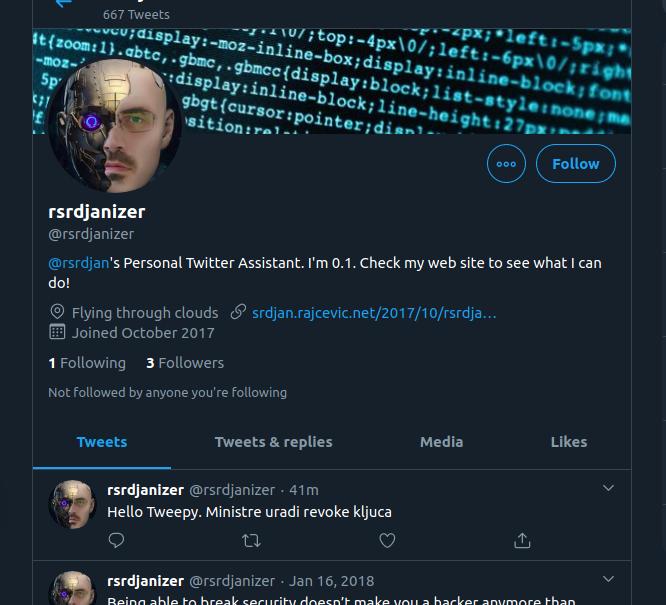 slika je jednim dijelom ministrova
slika je jednim dijelom ministrova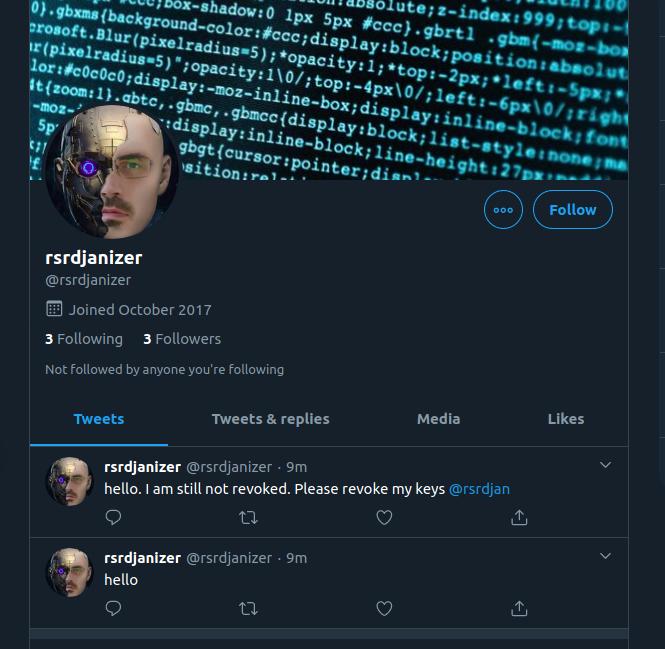


 twitter bot has a half picture of minister
twitter bot has a half picture of minister
