Vladimir Cicovic
Analiza moguceg napada na EU banke
REvil i Killnet
Napomena: Analiza je uradjena sa minimum informacija zbog nedostatka vremena (napad pocinje 16 Juna)
Izvor informacije za pomenuti napad: https://twitter.com/vxunderground/status/1669034104619245587
Tajnost operacije, tajnost mete/cilja, tajnost ucesnika operacija, tajnost pocetka operacije, tajnost lanca operacije
Resursi, brojnost grupe vs resursi i brojnost meta
TTP – tactics, tehnics procedures , ogranicen set TTP za operacije
Tajnost operacije
uspjeh bilo kakvog angazovanja u sajber prostoru utice najvise tajnost operacije. Tu se meta/zrtva bez vanrednih mjera osjeca sigurno u svakodnevnoj rutini i poslovima. Bilo kakav nagovjestaj operacije ugrozava istu jer suprotna strana se moze prilagoditi potencijalnom napadu i napadacu. Meta u slucaju prepoznavanja aktivnosti moze podici nivo angazovanja ljudstva, sredstava i ocekivanom ucinku napada. Ako se prepoznaje , recimo, da ce biti izvrsen DDOS napad na mrezu gdje se nalazi meta – iste se mogu ili prosiriti na nove (na nekoliko dana il sedmica) mreze/izlaze/ulaze ili angazovati dodatna sredstva da bi osigurali nesmetan rad. Ovo moze biti privremeno i vremenski ograniceno. Samim tim postoji mogucnost od neuspjeha napada.
Tajnost mete/cilja operacije
U slucaju otkrivanja mete/cilja opet dolazi do dodatnih angazovanja ljudstva, sredstava, vrsi se analiza kompletnog IT sektora, uspostavlja se rezim u kojem se (ograniceni period) vrsi zastita mete/cilja. Sav fokus ide na metu, analizu mete i rada iste – sa ciljem stvaranja modela gdje meta/cilj i dalje funkcionise. Npr kradja svih racunara u jednoj filijali banke – gdje se prave dodatne rezerve (na nekom drugom mjestu) i bekup radnih stanica/servera kroz ograniceni vremenski period.
Tajnost ucesnika operacije
Jedna od stvari uspjeha moze biti i tajnost ucesnika. U slucaju otkrivanja postoji mogucnost opstrukcije ili manipulacije ucesnicima. Ucesnici se mogu opstruisati tehnicki, psiholoski i fizicki. Tehnicki, sredstva izvrsenja: racunari, internet konekcije, struja. Psiholoski: izazivanje sukoba izmedju clanova grupe, stvaranja osjecaja krivice ili druge vrste manipulacija. Fizicki, likvidacija ili otmica.
Tajnost pocetka operacije
Ovisno o finalnom cilju prema meti – samo otkrivanje pocetka moze pomoci racionalnom angazovanju sredstava i propasti kompletne operacije. Mogucnost tajnih operacija druge strane kako bi finalno uticala na propast il ometanje napada.
Tajnost lanca operacije
Ovdje se uzima model ransomware grupe/DdoS. Citav lanac koji se koristi za operaciju
(ransomware treba IA initial access, C2 servere, C2 alatke i operatore za iste)
(DdoS koristi placene DDOS servise, osobe koje uspostavljaju sopstvene DdoS servise, novac/kriptovalute)
(remote exploit, ranjivost , 0day brokeri)
U slucaju da je poznat citav ovaj lanac koji se koristi za operaciju ili samo dio – pa samim tim mogu uticati na manji dio da napadaca onesposobe il onemoguce kako bi nastavio napad.
Initial Access: ubacivanje FBI agenata/agenata privatnih intel kompanija sa laznim pristupima odredjenim kompanijama. Uvodi se kompletna lazna IT struktura kompanije, ili se daje tacno pristup sa nalozima u kontrolisanom okruzenju – gdje napadac se onemogucava da napadne komplet IT strukturu vec samo onaj manji dio koji je u kontrolisanom okruzenju (izlovan, isklljucen sa glavnom dijela)
C2 serveri: ubacivanjem servera sa punom kontrolom nad napadacevim server side softwerom i onemogucavanjem rada u odredjenom dijelu operacija ili monitoring konekcija prema metama
C2 tools/alatke: prodaja bekdorovanih alata, monitoring, unistavanje kompletne infrastrukture
DDOs servisi: pridobijanje klijenata, laziranje napada (u dogovoru sa metom/ciljem)
DdoS servisi “trovanje”: ubacivanjem ogromnog broja DdoS servisa po povoljnim cijenama i radom bez problema – da bi se u toku perioda planiranog napada “ukinuo” ili lazirao napade na metu/cilj
Novac/kripto valute: izgradnja mjenjacnica od strane FBI/CIA/NSA/EU interpol – monitoring slanja/primanja izmedju kriminalaca. Ukidanje kompletnog protkola za odredjeni dio interneta ili glavniih ruting tacaka, DDOS kripto mjenjacnica, pronalazak ranjivosti u kriptovalutama/blokcejinu/pametnim ugovorima
Remote 0day exploiti: sama potraznja prema vrsti softwera moze ukazivati na mete. Od postavljanja 0day brokera, do informacije koji soft zele "napasti" - takve informacije vec mogu pomoci da se smanji broj meta i onemoguci napad
Resursi, brojnost grupe vs Resursi i brojnost meta
Najveci izazov za napadaca jeste da ako nema snagu da udari na metu/mete – izazove psiholoski efekat kroz medije/internet. Meta/cilj moze uraditi isto kroz medijsko eksponiranje i obesmisljavanje napadaca.
U slucaju da resursi i brojnost grupe veoma mala naspram resursa i brojnosti meta.
Ako postoji napad na odredjeni sektor – onda se servisi koji su onemoguceni mogu prebaciti na druge kompanije kroz legalan rad i sve ostalo (zakonski problem, regulative, al moguce)
U slucaju Killneta i Revil, dolazi do udruzivanje resursa al opet ne moze rezultirati uspjehom zbog brojnosti meta, geografske rasprostranjenosti i nepoznavanje rada banaka. Plan je napad je vjerovatno web servisi i slicno ali i tu postoji mogucnost postavljanja Anycasta na vise provajdera, dislokacija geo blokiranje i drugo. Banke su u vecoj mjeri spremne na ovakve stvari.
TTP – tactics, tehnics procedures , ogranicen set TTP za operacije
Odavanjem TTP odredjene grupe (recimo Anonymous Sudan, DdoS) dolazimo do fokusa i analize na detalje koji koriste i koje toolove koriste. Unutar rada i principa rada toolova je moguce pronaci odredjene slabosti. Npr DNS query, slanje paketa i drugo mogu imati ranjivu tacku. Primjer – postavljanjem *.meta.com na 127.0.0.1 za kveri iz Rusije ili VPN provajderima sirom svijeta moze dovesti do toga da napadac obori svoju infrastrukturu.
Mozemo koristiti za usporavanje napada, preusmjeravanje napada, laziranje uspjeha napada i slicno.
Moguce vrste napada na EU Banke
DDOS napad
Ovisno o koga napadaju - jedan dio napada Killnet i Anonimusi Sudana nije imao efekta. U slucaju Anonimusi Sudana koji imaju svoju infrastrukturu za DDoS + rentaju istu drugima za novac, mete biraju koje se nalaze iza cloudfare i slicnih servisa (zastita od DDoS) kako bi pojacali efekat napada u medijima. Male i srednje mete (male kompanije, kompanije sa manjim brojem ljudi i nedovoljnom anti-DDoS zastitom) pod DDOS napadom grupe Anonimus Sudan, uglavnom od 5 do 15 min. U nekim slucajevima i duze ali se radi o 1 serveru sa HTTP portom iza cloudfare kojeg je moguce oboriti sa manjim DDoS napadom. Nekoliko puta im je DDoS "propao" ili nisu bili u mogucnosti da odrze napad duze od 5 minuta (uglavnom mete koje su imale daleko bolju zastitu ili se bave cybersec)
Sve banke posluju SWIFTom, ATM mreza je povezana sa bazom u bankama ali moze biti izmjestena tako da se nalaze na razlicitim ISP/mrezama i da imaju "hibridni" pristup (kombinacija 4G mreze i racunarske mreze, ili wifi pristup)
Najranjiviji dio banaka su web portali - ali je moguce i taj dio zastiti ukoliko se preduzmu mjere na vrijeme ili se u toku napada donese odluka. Ovdje moze doci do prekida pristupa klijenata na web platformi (recicemo da pristup preko softwera na telefonima, desktop racunarima moze biti "izmjesten")
Ransomware napadi
Ovise od nekoliko faktora: Initial Access brokerima, raspolaganjem 0day exploita i brojem operatora a onda sam proces sinhronizacije napada (pricamo da zele da napad izvrse na sve EU banke). Banke ulazu u sigurnost svog IT sektora. Postoje mehanizmi na nivou kompletne banke gdje se vrsi izolacija servisa i njihovo osiguravanje da prilikom napada rade neometano ( high avaibility, replikacija servisa, bekupi i tako dalje). Sama jedna grupa ne bi bila u stanju da u kracem vremenu osigura pristup IT sektoru ovih banaka. Jedan od pristupa moze biti i insajderi unutar banaka koji bi pomogli za pocetni pristup ali i tu se nivo sigurnosti banaka razlikuje tako da nije sigurno da ce svi napadi proci uspjesno - ako se desi, to ce opet biti manji dio. Uspjeh napada zavisi od dosta faktora tako da opet su u nemilosti koliko je banka pripremljena u tehnickom smislu.
Medijsko promovisanje napada
Jedini siguran element u svemu ovome jeste psiholoski efekat navodnog napada. Cak i ako se ne desi napad, sama cinjenica da se informacija pojavila u medijima moze pomoci u jacem efektu kada se desi obaranje web sajta neke banke (recimo da je samo to cilj, najbrze za izvodjenje u ovom slucaju) . Od berze, gubitka klijenata, ostalo. Postoji mogucnost da se izazove izvlacenje novca iz banaka i tako izazove problem sa radom banaka.
Napada konkurenata
Ovako "sivu" situaciju mogu iskoristiti (ali je manje vjerovatno iz vise razloga) konkurencija odredjenih banaka da uniste one druge (kroz spinovanje, stvarne napade i drugo). Opet postoji mogucnost da se napadi povezu i da organizator napada (u ovom slucaju banka) bude pronadjen i dozivi propadanje/gubitak novca/zatvaranje. Tako da je malo il nikako vjerovatno. U slucaju da jeste, onda mozemo pricati o povezanosti banke sa Killnet/REvil grupom kroz udio vlasnistva banke(recimo da je neko iz Rusije vlasnik dijela neke banke). Opet postoji mogucnost pronalazenja veza grupa-banka konkurent.
Podrska strane zemlje grupama Killnet i REvil
Drzave cesto koriste kriminalne grupe zbog ostvarivanja odredjenog cilja. Ovdje postoji mogucnost umjesanosti Rusije kao sponzora. Takve stvari se mogu otkriti na osnovu toga koliko je grupa imala resursa prije i poslije odredjenog vremena. Kakav impakt njihovi napadi imaju (ne u medijima, vec tehnicki dio napada) i tu se moze naci povezanost u smislu da imaju dosta novca, da su bolje organizovani, da su promjenili nacine napada i drugo. Ali kao sto rekoh tako nesto postaje vidljivo. Da li mogu da ih usmjeravaju prema odredjenim metama? Da. ali opet u tom slucaju bi drzava osigurala da napad bude efektivan sto bi bilo vidljivo i lako za uociti.


 Foto: capital.ba
Foto: capital.ba

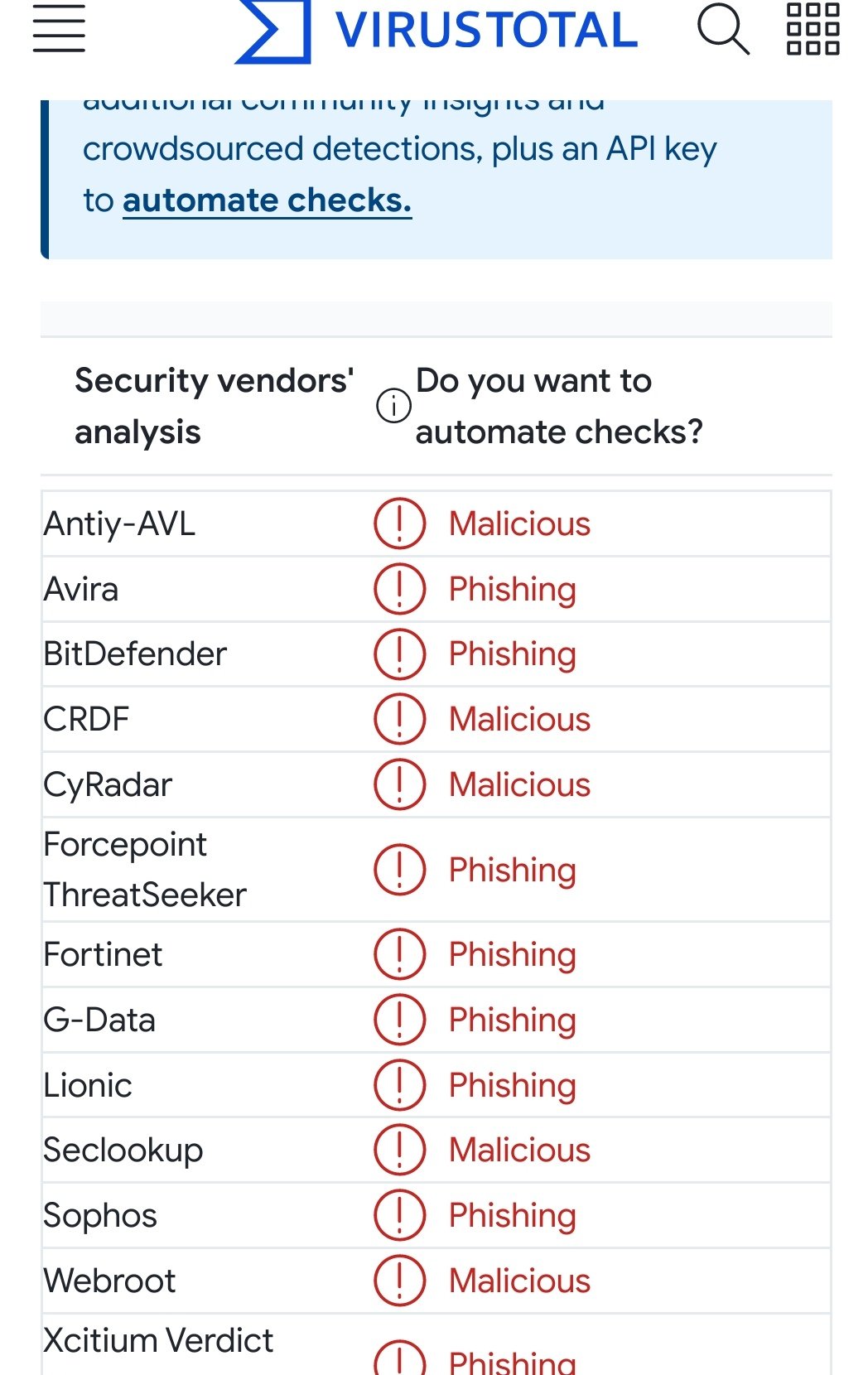
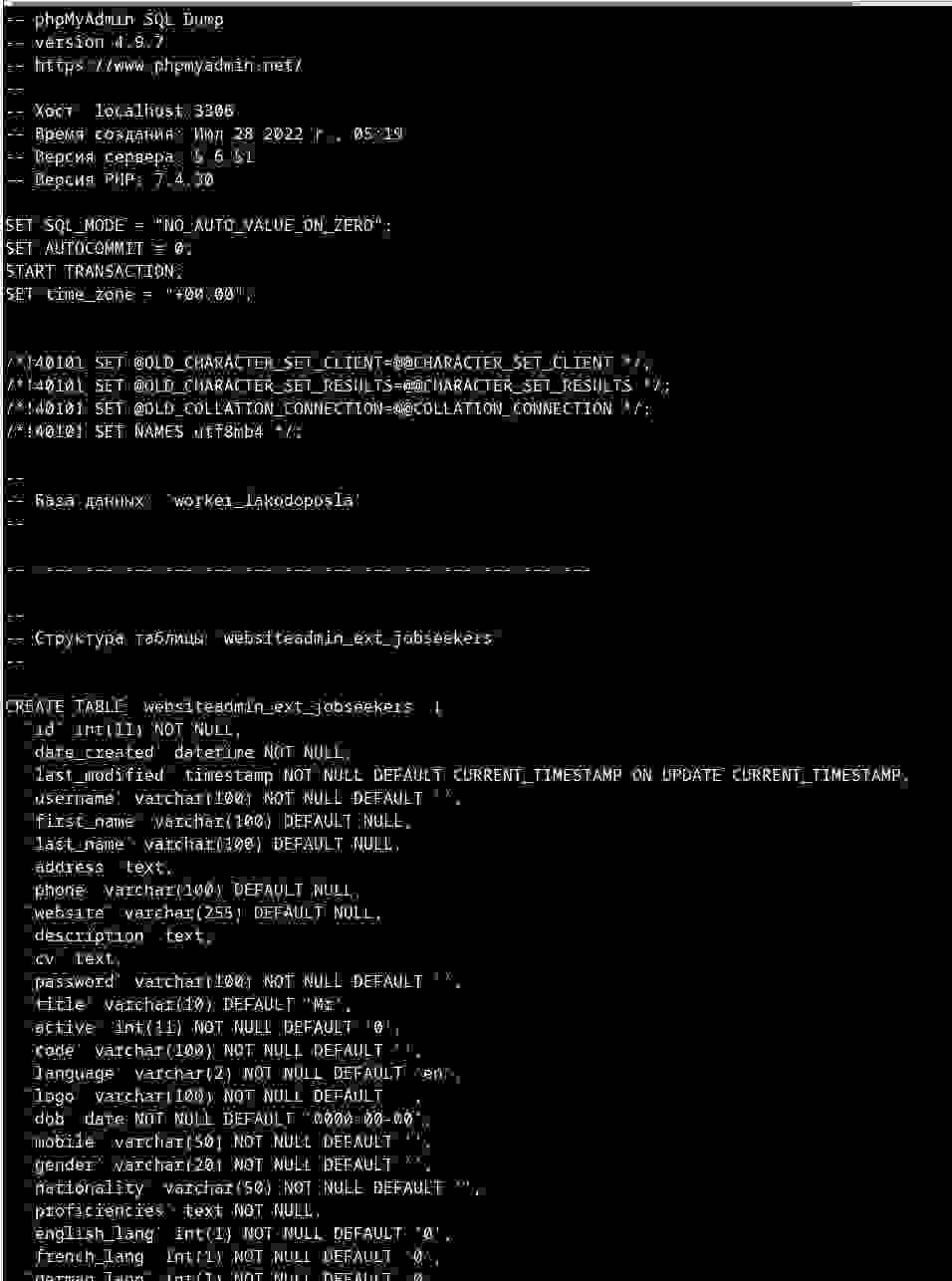 Slika zapisa baze
Slika zapisa baze
 freeOTP logo
freeOTP logo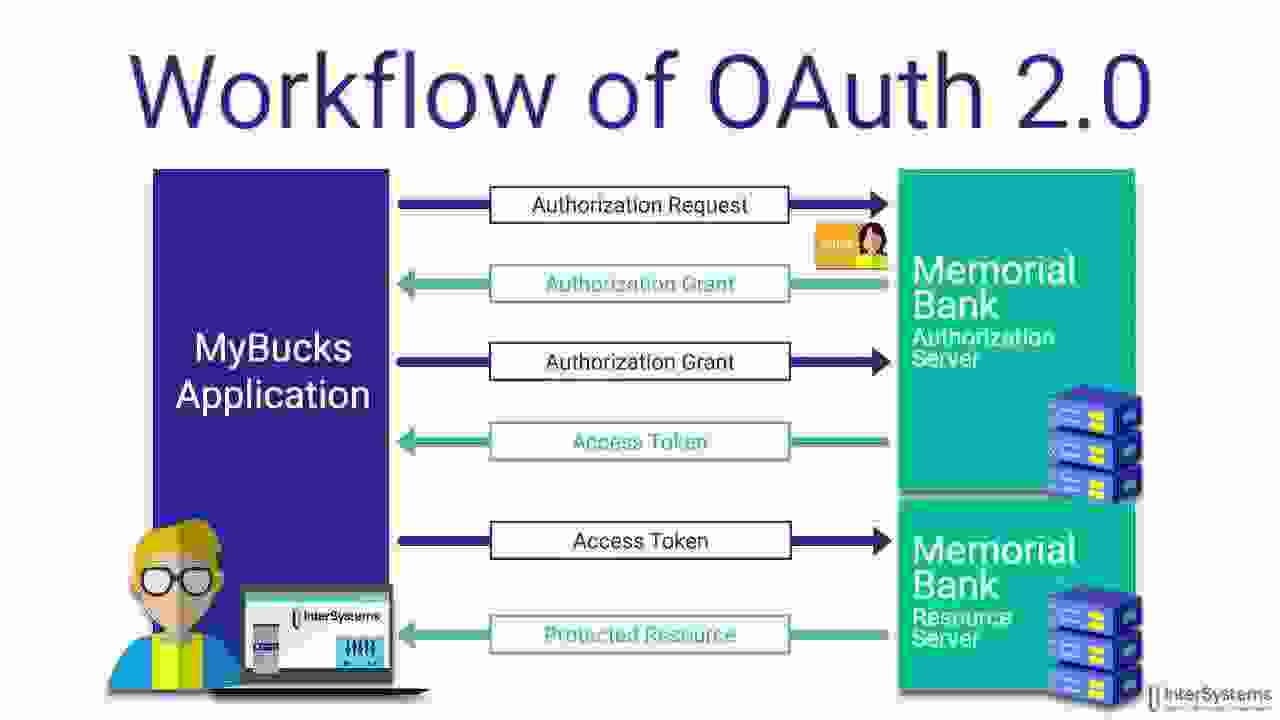 OAuth2 - slika preuzeta sa InterSystems Learning Services youtube kanala
OAuth2 - slika preuzeta sa InterSystems Learning Services youtube kanala
 Picture was taken from http://www.tankado.com
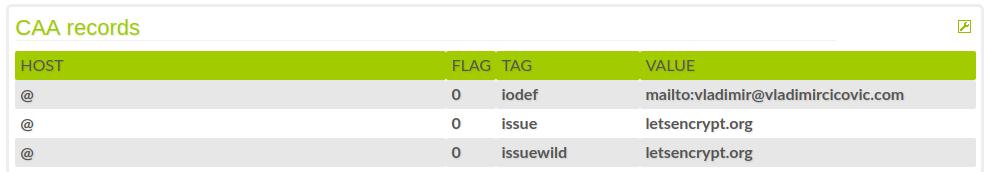
Picture was taken from http://www.tankado.com
 slika je jednim dijelom ministrova
slika je jednim dijelom ministrova


 twitter bot has a half picture of minister
twitter bot has a half picture of minister