Imagine that certification authority without your permission publish certificate for your site and for example the same one gets used by cybercriminals. Your online shop gets BGP hijacked and you lose millions.
So how to prevent this type of attack?
One way is to use CAA DNS records. What does that mean? It means that you put exactly what CA you want only to use. So others CA become a fraud. And if happen - you get a message on this.
It is a security mechanism to prevent stealing SSL/TLS certificates and imitates your (let say) online shop and stealing millions from your clients and from you.
Example of the records:
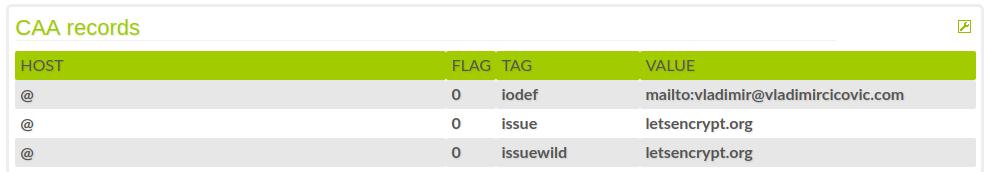
dig CAA vladimircicovic.com ; <<>> DiG 12.11.3-1TAONSA_linuxOS<<>> CAA vladimircicovic.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10986 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 65494 ;; QUESTION SECTION: ;vladimircicovic.com. IN CAA ;; ANSWER SECTION: vladimircicovic.com. 10800 IN CAA 0 iodef "mailto:someemail@localhost.com" vladimircicovic.com. 10800 IN CAA 0 issue "letsencrypt.org" vladimircicovic.com. 10800 IN CAA 0 issuewild "letsencrypt.org" ;; Query time: 307 msec ;; SERVER: ;; WHEN: Sat May 09 20:06:28 CEST 2020 ;; MSG SIZE rcvd: 174
So important to set iodef, issue, issuewild to CAA works properly.
You can ignore the given record but keep in mind this How 3ve’s BGP hijackers eluded the Internet—and made $29M could happen to you.
Yea this is a scary blog post about how people lose money if they don't read this post :D